Email Messages Containing Malicious File Removed After Delivery
Email Messages Containing Malicious File Removed After Delivery - When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Identify the ip address of a malicious email sender. Start an incident for further investigation. This article explains how to use threat explorer.
This article explains how to use threat explorer. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Identify the ip address of a malicious email sender. Start an incident for further investigation.
When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Start an incident for further investigation. This article explains how to use threat explorer. Identify the ip address of a malicious email sender.
Phishing/Malicious messages going through containing html attachments
Start an incident for further investigation. Identify the ip address of a malicious email sender. This article explains how to use threat explorer. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke.
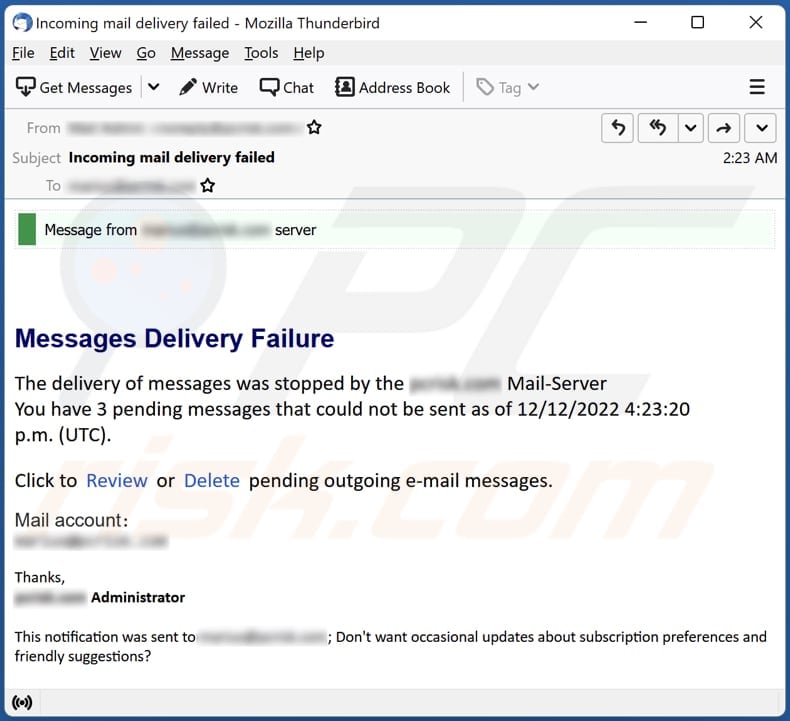
Messages Delivery Failure Email Scam Removal and recovery steps (updated)
Identify the ip address of a malicious email sender. This article explains how to use threat explorer. Start an incident for further investigation. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke.
Detects Malicious Email Attachments To Avoid Malware DroidCops
When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Identify the ip address of a malicious email sender. This article explains how to use threat explorer. Start an incident for further investigation.
I’ve Clicked On a Malicious Link or File, What Now? IT Consulting
Identify the ip address of a malicious email sender. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Start an incident for further investigation. This article explains how to use threat explorer.
Malicious RTF File (CVE202321716) Protection OPSWAT
Start an incident for further investigation. This article explains how to use threat explorer. Identify the ip address of a malicious email sender. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke.
Phishing/Malicious messages going through containing html attachments
When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. This article explains how to use threat explorer. Identify the ip address of a malicious email sender. Start an incident for further investigation.
Malicious spam with zip attachments containing .js files SANS
This article explains how to use threat explorer. Start an incident for further investigation. Identify the ip address of a malicious email sender. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke.
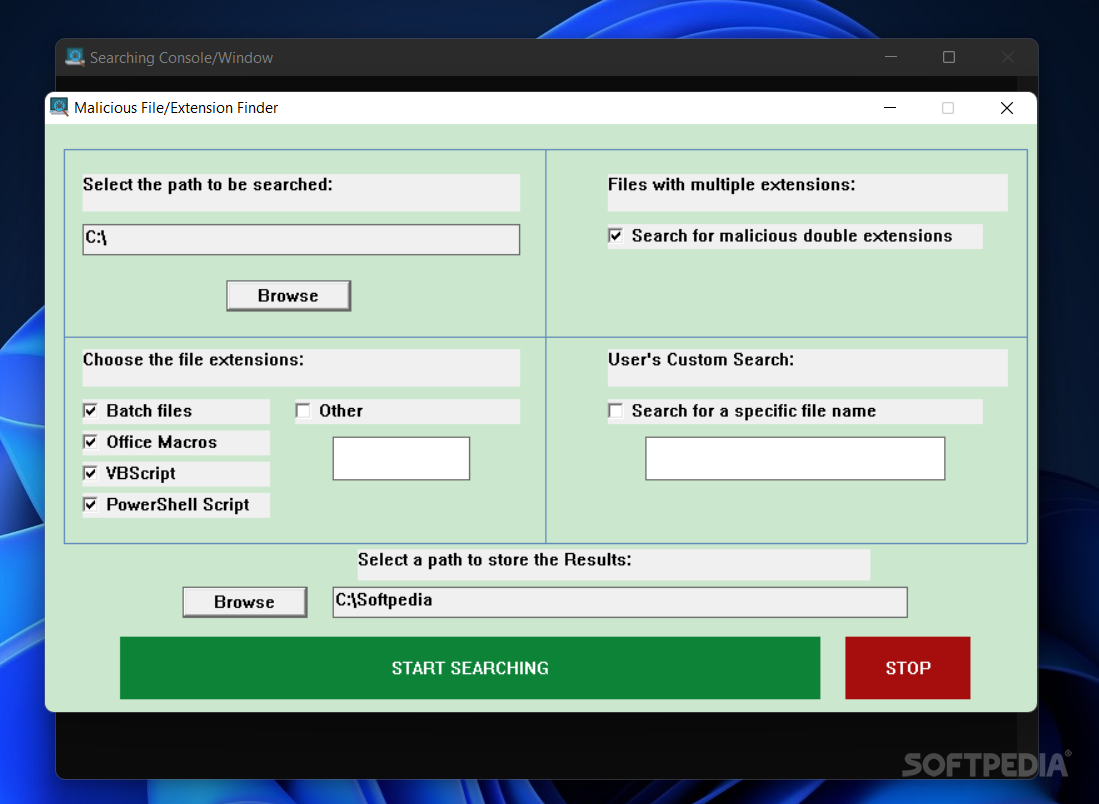
Malicious Extension/File Finder 1.0 Download, Review, Screenshots
Start an incident for further investigation. When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. This article explains how to use threat explorer. Identify the ip address of a malicious email sender.
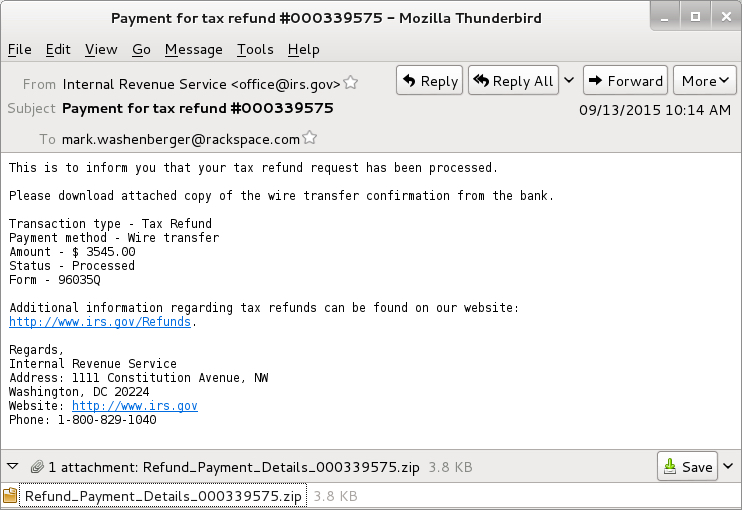
Email containing ‘payment advice note’ delivers malicious payload
When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Identify the ip address of a malicious email sender. Start an incident for further investigation. This article explains how to use threat explorer.
Messages containing malicious entity not removed after delivery r
When it comes to computer safety, if you have no need to click on a link, and defender is telling you it is malicious, it is probably best not to poke. Start an incident for further investigation. Identify the ip address of a malicious email sender. This article explains how to use threat explorer.
When It Comes To Computer Safety, If You Have No Need To Click On A Link, And Defender Is Telling You It Is Malicious, It Is Probably Best Not To Poke.
Identify the ip address of a malicious email sender. This article explains how to use threat explorer. Start an incident for further investigation.